Since the SamSam attacks that targeted US healthcare entities in March 2016, Talos has been concerned about the proliferation of ransomware via unpatched network vulnerabilities. In May 2017, WannaCry ransomware took advantage of a vulnerability in SMBv1 and spread like wildfire across the Internet.
Today a new malware variant has surfaced that is distinct enough from Petya that people have referred to it by various names such as Petrwrap and GoldenEye. Our source, Talos, is identifying this new malware variant as Nyetya. Our current research leads us to believe that the sample leverages EternalBlue and WMI for lateral movement inside an affected network. This behavior is unlike WannaCry, as there does not appear to be an external scanning component. Additionally, there may also be a psexec vector that is also used to spread internally.
The identification of the initial vector has proven more challenging. Early reports of an email vector can not be confirmed. Based on observed in-the-wild behaviors, the lack of a known, viable external spreading mechanism and other research we believe it is possible that some infections may be associated with software update systems for a Ukrainian tax accounting package called MeDoc. Talos continues to research the initial vector of this malware.
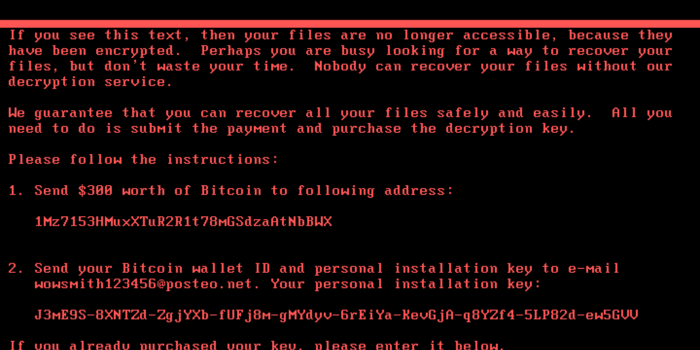
As with all ransomware, Talos does not recommend paying the ransom. With this specific piece of ransomware, it should be noted that the associated mailbox used for payment verification and decryption key sharing has been shut down by the posteo.de website. This renders any successful payment as useless – there is no method of communication available for this attacker to use to verify payments from victims or distribute decryption keys once ransom payments have been received. There is also no method used by the malware to directly connect to command and control for remote unlocking. Nyetya is less of a piece of ransomware (where it’s implied you get your data back by paying the ransom), and more of a “Wipe” system meant to simply erase systems.
Source : http://blog.talosintelligence.com/2017/06/worldwide-ransomware-variant.html